Security has to be a collective concern for all of us. Whether you’re an engineer or a receptionist, whether you are working in an office or from home, we all have a part to play in ensuring our organization, systems and data are secure. There are seven steps that we can all take to mitigate risks.
“Hackers are breaking the systems for profit. Before, it was about intellectual curiosity and pursuit of knowledge and thrill, but now hacking is big business.” This is a 2011 reflection from the late Kevin Mitnick who became famous for his high-profile arrest in 1995, leading to five years in prison for computer and communications-related crimes.
Where valuable data can be found, hackers will try to investigate, infiltrate, extract, and extort data, whether it’s for monetary gain or another reason. It could be a ransomware attack, as seen with WannaCry in 2017. It could be industrial espionage, as seen with Chordiant Software in 2010. It could even be on behalf of another entity, for a nation state, as seen with SolarWinds or for military secrets like with WikiLeaks.
This article has been written to cover the essentials about cybersecurity, to explain the “Circle of Risk,” and outline a number of simple steps we can all take to mitigate risks.
The Cost of Convenience
Earlier this year, major U.K. retailers Marks & Spencer and the Co-op experienced empty shelves in their stores following a cyberattack, with the luxury department store Harrods also targeted. M&S paused online orders for an extended period which, drastically affected profits, as roughly one-third of M&S clothing and household goods sales in the United Kingdom are through online platforms.
These sorts of attack exacerbate the dependency that modern consumerism puts on online functionality. We are used to ever-present access to online shopping, always within our virtual reach. That ability to connect and communicate globally comes hand-in-hand with a steep decrease in our collective digital safety.
The M&S example is a microcosm for the way that we interact with the digital world today. As we become more connected than ever before, the risks that we face will grow in turn, and it’s impossible to ignore said risks when modern networks may tether everything, from banking mainframes to office computers and to baby monitors and pacemakers. Yes, the mainframe is the most securable IT platform in the world, but that doesn’t make it impenetrable, especially when there are so many outlying aspects, and a chain is only as strong as its weakest link.
Data Privacy and Internet Distrust
Privacies we may have previously taken for granted are steadily exploited in exchange for frictionless convenience. On the one hand, we can message seamlessly between devices and make VOIP calls across continents. On the other, we are more at risk of malware and phishing. Artificial intelligence (AI) brings new threats alongside new ways to counter them. Is it any wonder that increasing numbers of people believe their data is less secure than ever?
This mistrust is longstanding, as exemplified by a 2019 survey by Ipsos for the Centre for International Governance Innovation, with UNCTAD and the ISOC: 78% of respondents across 24 countries were concerned about online privacy, with about two fifths of those respondents being “very concerned.” Furthermore, one in four respondents claimed that they did not trust the internet.
The perception is that large companies do not take security seriously enough, and many are certainly unaware of breaches until it’s too late and personal data has already been compromised, stolen, and leaked. We must be actively conscious about our own security, and what we can do ourselves.
The Circle of Risk
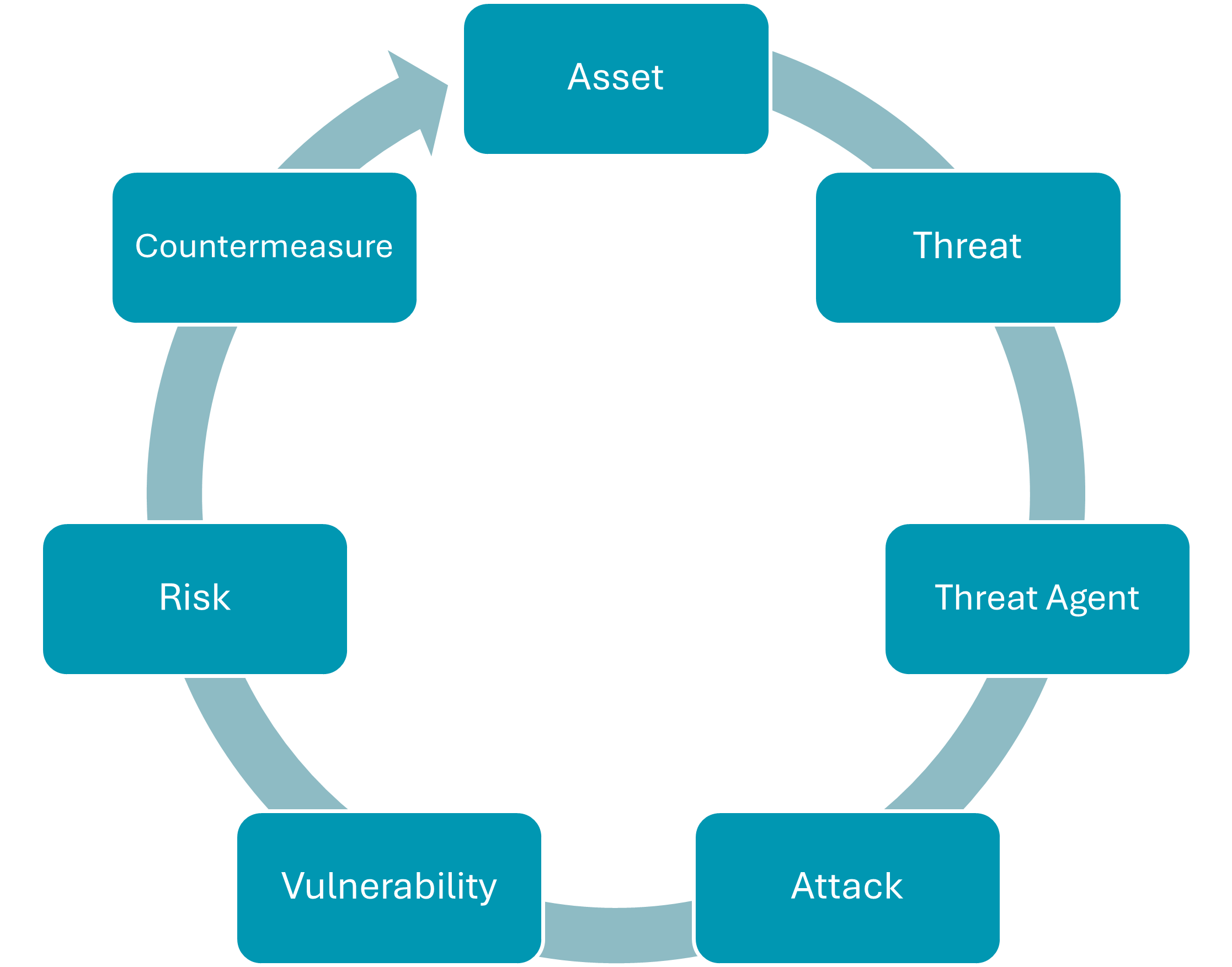
Assets are compromised by threats, perpetrated by threat agents who attack a system by exploiting vulnerabilities: This is a risk that can be mitigated with countermeasures that aim to protect assets.
Cybersecurity 101: The Circle of Risk
In cybersecurity, terms like “risks” and “threats” are bandied about but it’s not always clear what they mean, especially out of context. To that end, it’s useful to understand the terms used in the “Circle of Risk,” which is a graphical definition1 of the core security aspects involved in threat modelling. Said graphic may be used as a holistic framework in the management of cyber risks across various industries.
- Asset: something of value to a business that requires protection, which could be anything from a computer file, intellectual property, or hardware device. Assets may be compromised by…
- Threats: something that could result in the damage, destruction, alteration, or loss of an asset. These may be malicious in nature, they could be accidental, or something else like a natural disaster. Threats may be perpetrated by…
- Threat Agents: a person that means harm to an asset, such as a bad actor who directly hacks into a bank, or the system the hacker may use to cause damage, like a DDOS attack. Threat Agents may carry out…
- Attacks: the damage, destruction, alteration, or theft of assets. As mentioned previously, this attack could be malicious, but it could also be accidental (e.g., spilling water on a laptop). Malicious attacks often follow the exploitation of…
- Vulnerabilities: a weakness or absence of a safeguard/countermeasure, which threat agents will attempt to exploit. Vulnerability can be because of a flaw in programming (e.g., zero-day exploits) or something else (e.g., social engineering). Vulnerabilities expose you to…
- Risks: the possibilities of something bad happening, whether accidental or malicious. Risks can be mitigated by…
- Countermeasures: methods of control and protection, often in three forms — physical, administrative, and technical. These help to protect Assets. And so, the circle continues.
7 Simple Steps That Everyone Can Take
What seven steps can we all work towards, regardless of role, to improve security in the face of increasingly sophisticated cybercrime? It’s one thing saying that security should be a concern for all of us, but how do we go about achieving that in practical terms?
We can start by empowering our colleagues, teams, family, and friends with know-how to help keep systems and data secure. In that spirit, here are seven tips that can make a big difference:
- Protect sensitive materials to prevent sensitive information from being leaked or manipulated (e.g., tighten ACLs and encrypt data).
- Restrict users to only have what they need, only for as long as they need it (i.e., least privilege).
- Keep systems up-to-date with patches installed to fix any vulnerabilities and to prevent exploits (i.e., updates).
- Train staff on avoidance of suspect hyperlinks, downloading of files from untrusted websites, or inserting suspect USB sticks/CDs or even peripherals to your devices (i.e., training about phishing and malware).
- Keep an eye out for suspicious activity and remain vigilant in escalating this, so security staff may lock-down any users that engage in suspect behaviors (i.e., revoking and quarantining).
- Maintain event-logs, audit trails, and transaction history so discrepancies can be tracked and investigated if necessary (i.e., activity monitoring).
- Regularly undergo penetration (“pen”) testing and vulnerability assessments utilizing the talents of offensive “red team” staff who can think like a threat agent (e.g., OSINT, NMAP, and MITM) and find vulnerabilities to exploit (i.e., offensive testing).
Following these seven steps, any areas of weakness should be identified and remedied. This may involve training staff, refining policies, implementing new restrictions, or all of the above. The ultimate goal is for everyone to help fortify the system, rather than putting the onus of responsibility solely upon a CISO team.
Security as a Mindset
Looking ahead, organizations need to focus on understanding the changing nature of the cyber threats they face. Training should be provided to all staff and changes should be made to working cultures so we can “shift left” the presence of security. By performing these tasks at the "left" of the development lifecycle, issues are identified and resolved sooner, leading to reduced costs, improved quality, and increased efficiency.
Additionally, organizations should work to embrace (at least) the following three cybersecurity principles:
- Role-Based Access Control (RBAC) - Employees’ job roles should correlate with the types of access they are granted, which would ideally be used in conjunction with resource classification, with different teams/departments having different permissions to different resources.
- Least Privilege - User access is limited to the absolute minimum level that is required to perform their job functions, and only allows users to access the resources they need, when they need them
- Zero Trust (i.e., perimeterless security) - Users and devices are not trusted by default, with strict access controls being established, wherein verification is required for every access request. Every user and device must be authenticated before being granted access to any resources.
With these principles in mind and the seven steps implemented, your organization will be well on its way to mitigating risk. Please play your part to make the mainframe ecosystem more secure for all of us.
1 Laorden, Carlos & Sanz, Borja & Alvarez, Gonzalo & Bringas, Pablo. (2010). A Threat Model Approach to Threats and Vulnerabilities in On-line Social Networks. 85. 135-142. 10.1007/978-3-642-16626-6_15.
Security Consultant, IBM Champion, TechChannel Rising Star and a recipient of the Planet Mainframe 2025 Mainframe Influencer award, Niall Ashley has rapidly established himself in the mainframe space. A frequent speaker at conferences, committee member of GSUK, and STEM Ambassador, Ashley is also a mental health advocate and is a qualified suicide first-aid trainer.