Any effective data security system needs to be built as an integrated and intelligent security immune system, according to Julie Bergh, World Wide Lead Z Security Champion for IBM.
“The mainframe is the most securable platform out there, but today’s technologies – cloud, internet, mobile, big data, and so on – have eliminated ‘mainframe isolation,’” Julie explained. From a data protection and compliance perspective, this makes things more complicated. How do you manage, or even figure out, what’s going on in your environment? That’s why it’s so important that your security environment is always evolving.
According to Julie, security once mainly consisted of perimeter controls: deploying static defenses to guard or limit the flow of data, including firewalls, antivirus software, and web gateways. Around a decade ago, the security landscape evolved to include security intelligence, which leverages analytics to collect and make sense of massive amounts of real-time data flow, prioritizing events, and detecting high-risk threats in real-time.
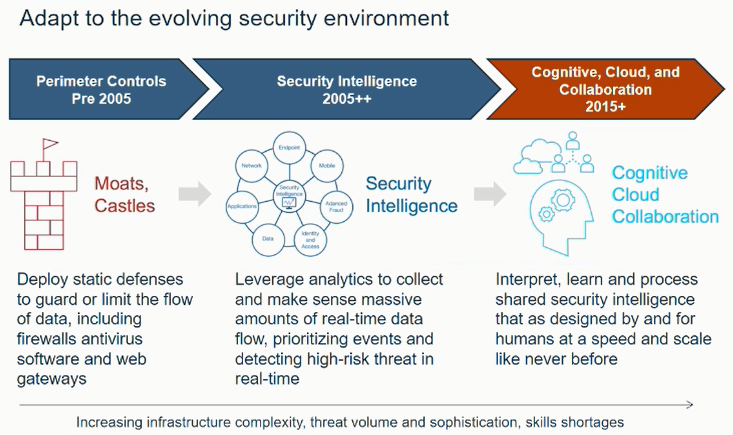
Most recently, the cognitive element came onto the scene. Julie calls this “Cognitive, Cloud, and Collaboration.” Cognitive security allows you to interpret, learn, and process shared security intelligence that was designed by and for humans at a speed and scale like never before.
Now, Julie says, your security environment should incorporate all three elements. You’re still using perimeter controls, taking in all of the relevant information, looking at anomalies, and using security intelligence, but it’s all from a cognitive approach.
In a presentation at SHARE® Providence, Julie explained why security intelligence alone isn’t enough, and discussed cognitive security practices that can take your security environment to the next level.
From Security Intelligence to Cognitive Security
Security intelligence provides actionable and comprehensive insight for managing risks and threats. The real-time collection, normalization and analytics of all mainframe data is especially useful to security analysts. Security analysts can gather information from a variety of sources, like log management, security information and event management (SIEM), network monitoring, risk management, and forensics, and then make intelligent security decisions based on that data.
For example, SIEM products give security analysts the ability to view security events and drill down into events in real-time so they can get the detailed information needed to make informed decisions.
This kind of transparency is key, but Julie explains that security teams often just see noise. It’s not always clear what action they need to take. Plus, investigating each incident requires a very time-consuming threat analysis.
Cognitive security helps solve this challenge. Mainframes now have the option to send real-time z/OS security events to Watson security analytics that utilize QRadar for enterprise-wide threat reporting and remediation. Watson unlocks a tremendous amount of security knowledge, looking at research reports, threat databases, security textbooks, vulnerability disclosures, and other sources in conjunction with your mainframe data to determine what’s occurred and where you need to be headed. Watson can also perform cognitive exploration of suspicious activities and behaviors, identifying the root cause and any additional indicators.
User behavior analytics (UBA) are another helpful cognitive security tool. UBA drills down to see the specifics of user activity, such as where users log on and log off, to glean actionable insights. From monitoring intellectual property to investigating compromised credentials, UBA gathers and analyzes the data and sets up alerts for security response.
Ultimately, security has evolved very quickly very fast, moving from basic perimeter controls (like firewalls or antivirus software), to modern security intelligence technology (like analytics-driven real-time threat detection software) to tomorrow’s cognitive security solutions, Julie explained. Adapting to this rapidly changing security environment gives your enterprise the best protection, and the best chance to ensure your company’s name isn’t mentioned in the headlines because of a security breach.
To learn more about cognitive security and the evolving mainframe security landscape, watch the full video from Julie Bergh’s “Enhanced Mainframe Cognitive Security” presentation in the SHARE Content Center.