“Engineering” is derived from the Latin ingenium, which means "cleverness."
With that in mind, any security engineering (SecEng) role should be considered a thinking role. Any SecEng needs to understand many security-related concepts, such as IT security, physical security, and personal security, and they would normally have one or more recognised accreditation that covers security audits and/or risk management, as well as deep technical understanding of the platform they primarily work on. But although a SecEng's main tasks relate to mainframe security, the role encompasses much more. Essentially, security engineers design processes that others must then follow.
SecEng interfaces with many different departments, as can be seen in the diagram below:
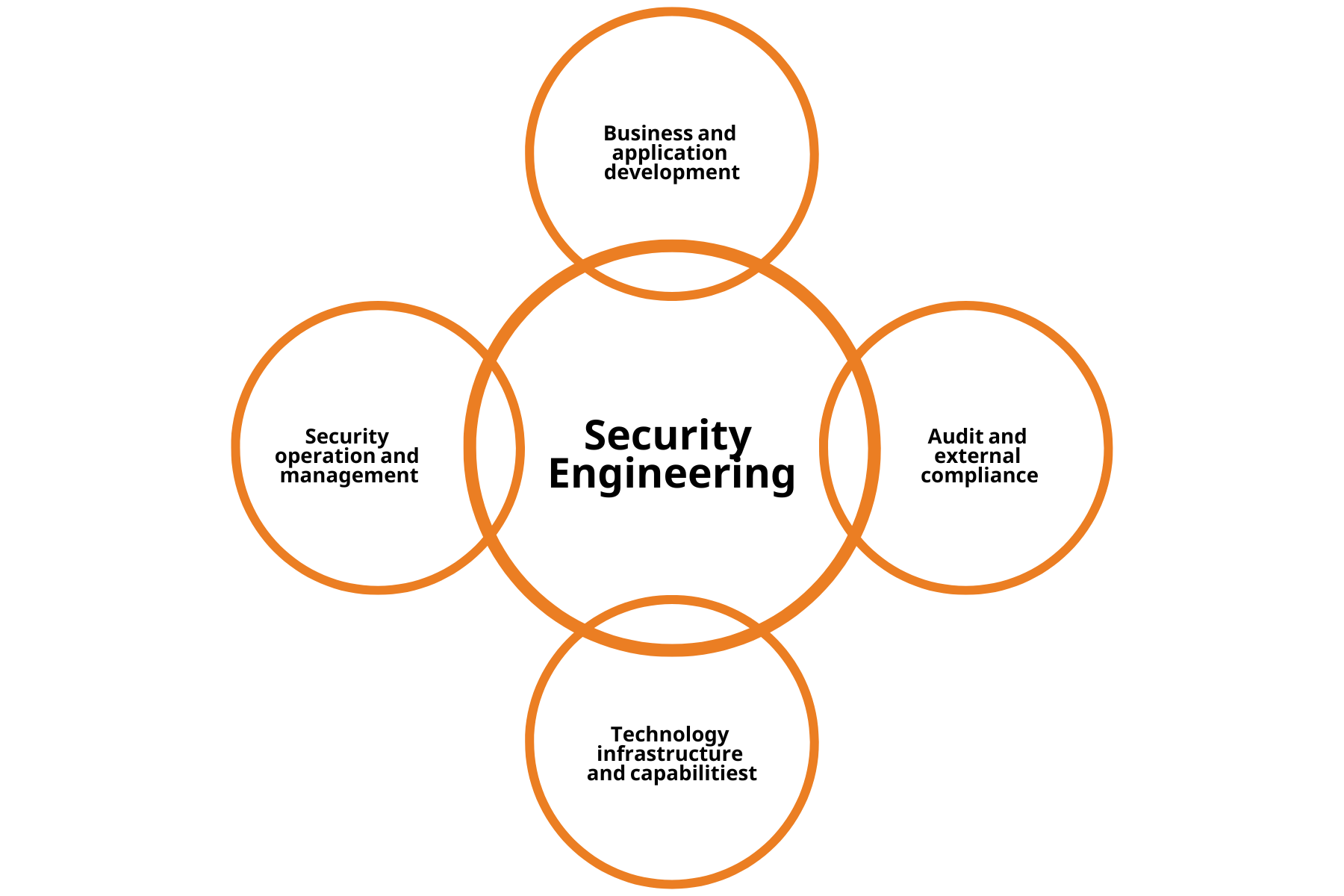
Security engineers gather information from all of the above sources and make recommendations to management. This ensures security is examined in a holistic sense. In contrast, a piecemeal approach to security is likely to leave gaps, which are rich for exploitation.
Key Security Engineer Responsibilities
Like other engineers, SecEngs build things. Just as a civil engineer builds bridges, SecEngs build security solutions. Responsibilities for a SecEng team typically include:
- Design, build, implement, and monitor security measures for the protection of mainframe systems, networks, and information
- Identify and define mainframe security requirements
- Design the mainframe security architecture and develop detailed cyber security designs
- Prepare and document standard operating procedures and protocols
- Develop technical solutions and new security tools to help mitigate security vulnerabilities and automate repeatable tasks
- Ensure that the organisation knows as much as possible as quickly as possible about security incidents
- Write comprehensive reports including assessment-based findings, outcomes, and propositions for further mainframe security enhancements
- Establishing security standards and best practices that an organization should follow
- Evaluating an organization’s systems, networks, and data to determine what types of security protocols are necessary
- Implementing security controls to protect an organization’s infrastructure and digital files
- Responding to any security breaches or intrusions that may occur
- Conducting scans and testing to identify any vulnerabilities
- Assisting with investigations to determine how security breaches happened
- Reporting findings and providing security recommendations to management
A security engineer understands that security needs to be baked into systems, rather than poured over them like gravy at the end. They also understand threat and technology changes in the marketplace, take a risk-based approach, and show where mitigation is needed. Quite often, the SecEng team oversees highly critical security processes, such as master key changes.
External Security Managers (RACF, ACF2, and Top Secret)
External Security Managers provide the tools to help the installation manage access to critical resources.
Any security mechanism is only as good as the management control of the people who access the system. Access, in a computer-based environment, means the ability to do something with a computer resource (for example, use, change, or view something). Access control is the method by which this ability is explicitly enabled or restricted. It is the responsibility of the installation to see that access controls that are implemented are working properly, and that variances are reported to and acted on by management.
Computer-based access controls are called logical access controls. These are protection mechanisms that limit users' access to information to only what is appropriate for them. Logical access controls are often built into the operating system or can be part of the logic of application programs or major utilities, such as database management systems. They may also be implemented in add-on security packages that are installed into an operating system.
To be effective, access control must allow management to adopt the principle of least possible
privilege for those resources that are deemed to be highly sensitive. This principle says that access to these resources is controlled in such a way that permission to use them is restricted to just those people whose normal duties require their use. Any unusual use of the resource should be approved by an administrator or manager, as well as the owner of the resource.
From a mainframe perspective, there are three solutions available. RACF from IBM and ACF2 and Top Secret from Broadcom.
Mainframe Security & ESMs
When handling mainframe security and the chosen ESM, the SecEng role tends to focus on the following items:
- Handle everything ESM related, such as design and structure of the security databases, naming conventions and standards, and internal database structures
- Build security and decide how infrastructure should be secured, using CICS, Db2, MQ, and generic IDs
- Develop change control standards
- Sign-off on security design for projects / provide sign-off on what is implemented for projects
- Design and own monitoring requirements, such as:
- What devolved security administration areas do
- User access reviews
- UserID reviews — monthly recertifications
- Generic ID reviews
- Quarterly for privileged
- Annual for non-privileged (protected users)
- Annual review of Role Based Access Control (RBAC) access
- Authorizer reviews
- Compliance reporting
- Manage a tool set
- Own relationship with vendors
- Conduct product selection and testing
- Leverage the current toolset
- Engage with internal audit for audits requiring ESM reports and guidance:
- Provide evidence (e.g., ESM reports) to internal audit when requested
- Provide input/response on any audit exceptions, findings etc.
- Work with technical teams to address any audit findings
- Own and remediate of any security-related risks
- Work with technical teams to address any ESM related risks
- Track resolution of SecEng owned risks
- Pro-actively identify any new risks
- Define what privileged access is for mainframe systems
Summary
The role of a security engineer as previously mentioned is a “thinking” one that is focused on identifying gaps in the deployed security controls and processes so that any threats can be identified and remediated. Their work applies to much more than just mainframe.
Other Reading and Links
Click on the links below and learn more about the role of the Security Engineer in the wider IT landscape.